Protecting Data by In-vehicle Edge Processing -DENSO’s “in-vehicle blockchain technology” surpasses conventional tampering detection techniques-
On September 2, 2021, DENSO Tech Links Tokyo #12, an event organized by DENSO Corporation, was held as a webinar. How will blockchains change our lives? Xin Xu explains the details of “in-vehicle blockchain technology,” which has been developed by DENSO, an automotive module manufacturer.
【Speaker】
Xin Xu
Information Traceability Dev. Sect., Solution Planning for Smart City Dept.,
DENSO Corporation
In-vehicle Blockchain Technology
Xin Xu: I’m Xin Xu of DENSO Corporation, and I’m leading a group in charge of blockchains, traceability technology, and business development. Today, I will introduce “in-vehicle blockchain technology,” which DENSO has been working on for the in-vehicle field.
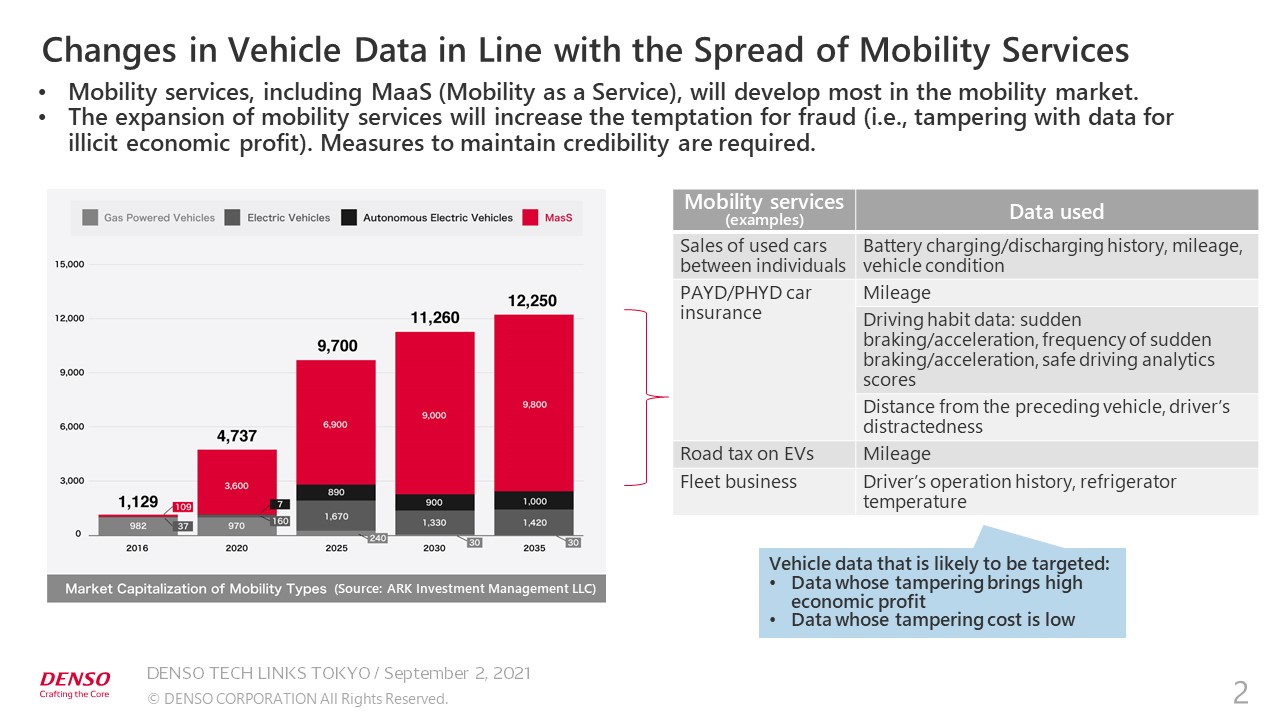
The auto industry has been undergoing a once-in-a-century paradigm shift, with a transition from car ownership to car use. This graph shows that MaaS (Mobility as a Service) will develop most in the mobility market, including EVs and automated driving. MaaS includes smart car dispatching services, such as Uber, telematics car insurance, such as Pay As You Drive (PAYD) and Pay How You Drive (PHYD), and sales of cars between individuals, which is still rare in Japan but has become increasingly popular in China.
As EVs spread, new taxes, such as the road tax on EVs, will be levied. The services which I mentioned earlier will be offered based on various types of in-vehicle sensor information or analytics information. High-accuracy information will help produce high-quality services. As such business spreads, unauthorized access and use will increase.
Previously, unauthorized access to vehicles was mainly intended to steal the safe driving data and personal data. However, the expansion of mobility services will increase the motivation for fraud, such as tampering with the data for illegal economic gain. For example, the mileage and accident history may be tampered with to increase the sales price of used cars, or a driving history that is disadvantageous for paying insurance premiums may be deleted.
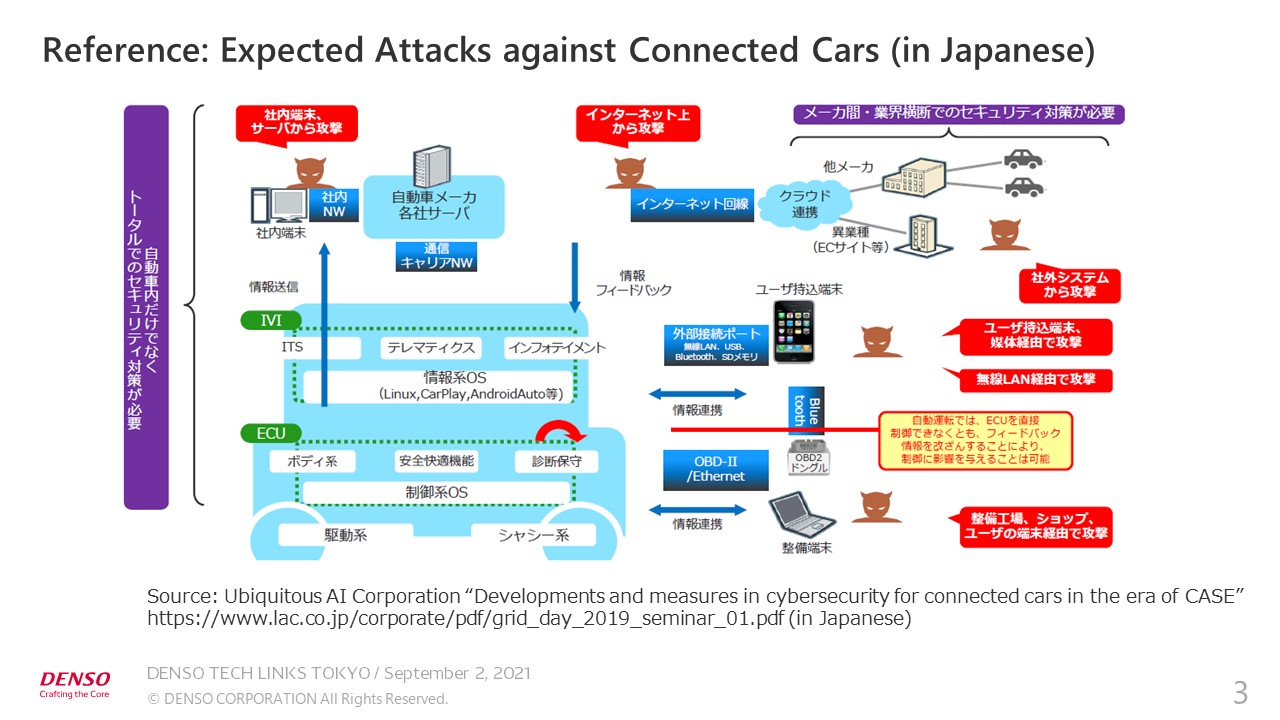
Such unauthorized access will evolve as connected cars spread. According to a document prepared by a security company, cyberattacks are carried out from various entry points, including the public Internet, servers used in service management systems, devices used by attackers, and maintenance diagnosis interfaces.
Three Categories of Unauthorized Access to Vehicles
We have classified these threats into three main categories. The main threats are attacks to tamper with the vehicle data, followed by attacks against vehicles by a third party, and inside jobs by an owner and physical invasion by a third party.
Let’s take a look at specific cases of tampering. As computerization of vehicles has progressed, attackers now hack passwords and take advantage of vulnerabilities in the operating system to use the root authority by masquerading as authentic users and tamper with the data. Customers have often told us that it is very difficult to cope with data tampering by vehicle owners or via the physical interface. Taking measures to prevent tampering increases the manufacturing and operational costs.
Regarding ensuring the integrity of vehicle information, it is often said that the problem can be solved by uploading the vehicle data to the cloud and registering the data in blockchains in the cloud. Currently, however, communication between vehicles and between a vehicle and the Internet is often unstable depending on the location, making it difficult to upload the data to the cloud immediately.
Even if data is stored in a vehicle for a certain period, there are risks of tampering. In other countries, the vehicle ecosystem is well developed and various in-vehicle apps are used. Locally stored shared data may be tampered with by third-party apps, which require real-time access.
Preventing Tampered Data from Being Offered for Services
To address this issue, instead of ensuring complete security, we set the goal of not offering tampered data for services or not uploading it to the service servers. Our idea that blockchain technology could be used on the vehicle local side led to the development.
Obviously, in-vehicle computers are not so powerful and cannot handle full blockchains. For this reason, we used basic blockchain mechanisms including distributed ledger and hash technologies, and embedded technology to ensure coordination with DENSO’s excellent hardware.
The vehicle data, which is input into a computer, is processed into hash chains. The secure area of in-vehicle devices is used to distribute and store part of the hash value. When new data comes in, tampering can be detected based on the consensus of both areas.
Vehicles as Cost-sensitive Products
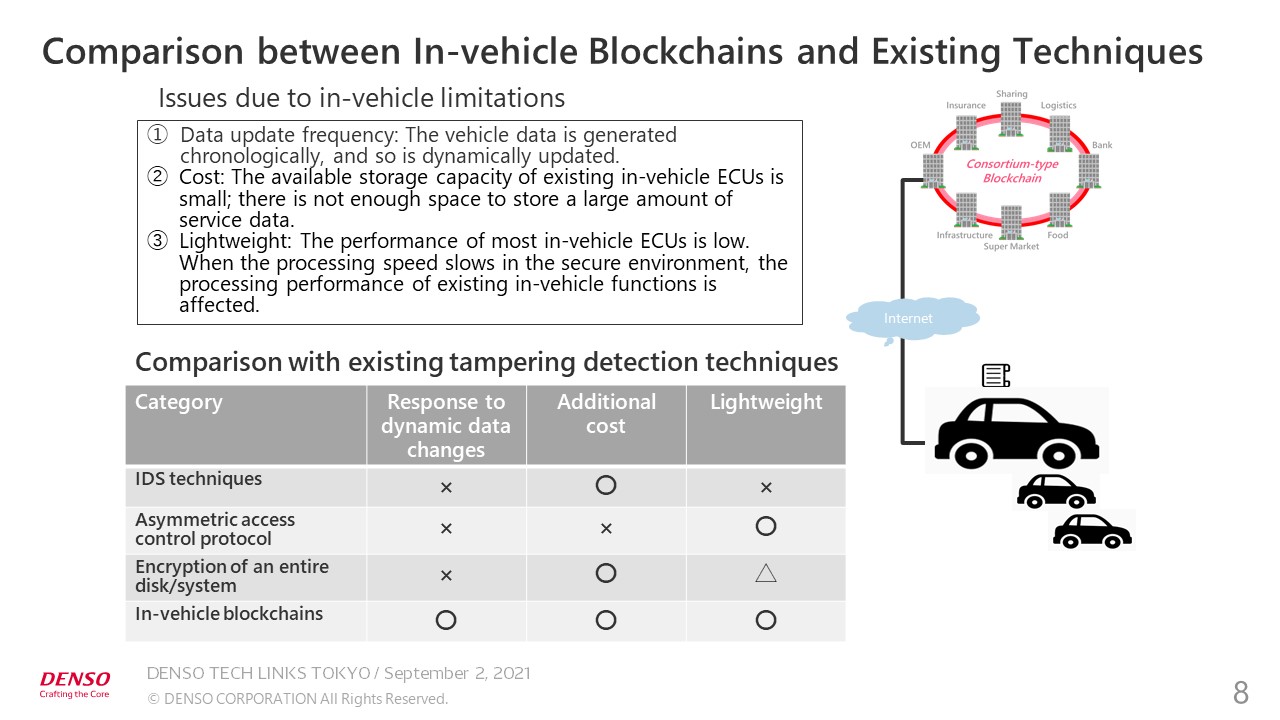
As I have explained, tampering can be detected locally by using in-vehicle devices. However, I’m often asked: “Why is it necessary to take the trouble to use blockchains ?” My answer is: to cope with the many limitations of vehicles. Vehicles are equipped with many sensors and time series data is generated frequently. Conventional methods of detecting tampering are somewhat weak.
Vehicles are highly cost-sensitive products. It is extremely difficult to use storage devices which can securely store a large amount of data. It is also crucial to make the in-vehicle software lightweight. ECUs must process other data, so only a few percent of CPU power can be allocated to detecting tampering.
Our in-vehicle blockchain technology has an advantage over conventional techniques of detecting tampering in in-vehicle applications. The evaluation results may vary when the difficulty of application to non-vehicle devices and the complicated installation process are taken into account. Nevertheless, our technology has these advantages in the in-vehicle field.
We have also been developing a mechanism to store important information in multiple in-vehicle devices, instead of a single device, and a mechanism to distribute and store the V2V data using blockchains in anticipation of the vehicle architecture in the future. Obviously, in-vehicle blockchains represent only one of the modules, and our in-vehicle defense-in-depth technology and other security mechanisms must also be used to protect the vehicle data.
Linking In-vehicle Blockchain Technology with Consortium Blockchain Technology
By linking in-vehicle blockchain technology with consortium blockchain technology, we have achieved the world’s first mechanism to enable local protection of the vehicle data on the edge side, direct registration of data required for services in the inter-company blockchains, and end-to-end (E2E) data protection by using in-vehicle blockchains.
In the mobility service field, we can propose mechanisms for smoothly protecting customers, including automakers, used car assessment companies, and insurance companies, or for providing partial protection. In terms of value proposition, we can ensure local data reliability of in-vehicle devices, including drive recorders, which can increase the value of vehicles equipped with these devices.
We can also offer various solutions to ensure smooth data protection from the edge side to the cloud. Servers can be used to process all the vehicle data, but customers often say that keeping all the data in servers would increase server running costs and that they want to reduce data communication costs. We can propose data protection solutions based on in-vehicle edge processing.
This concludes my presentation about DENSO’s efforts to develop in-vehicle blockchains.
Thank you very much.