Cybersecurity
As mobility and automotive connectivity accelerate in the global marketplace, the risk of security threats increases. Automotive command systems are facing a growing risk of breaches that would give hackers control of the vehicle or that could cause a potential malfunction of the in-vehicle system. To protect consumers and their vehicles from cyber threats, DENSO provides continuous updates to our advanced security technologies.
Feature
Attack Prevention and Damage Mitigation
To prevent attacks from the outside, DENSO has developed a defense-in-depth system. This comprehensive security system monitors the full in-vehicle technology, protecting it with four layered functions: authentication for external connections, a secure gateway to keep the vehicle intact, authentication to enhance in-vehicle local area network (LAN) security, and electronic control unit (ECU) protection.
In addition, DENSO protects customers with resilient security technology, coordinating with an external security center to ensure early detection, judgement and recovery, and to quickly minimize damage in the event of a known/unknown cyber attack.
Technology
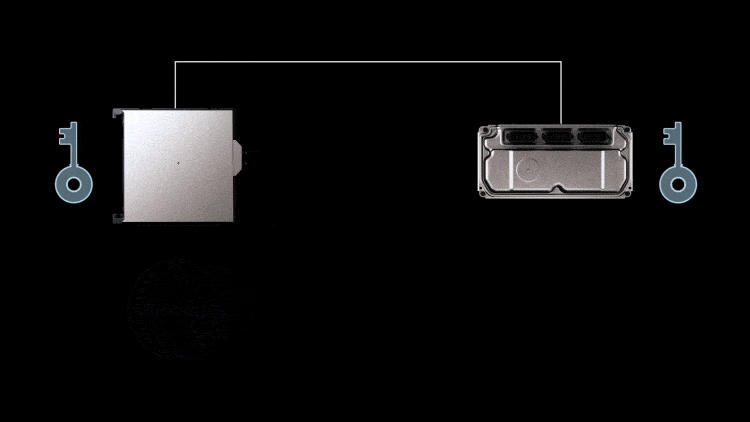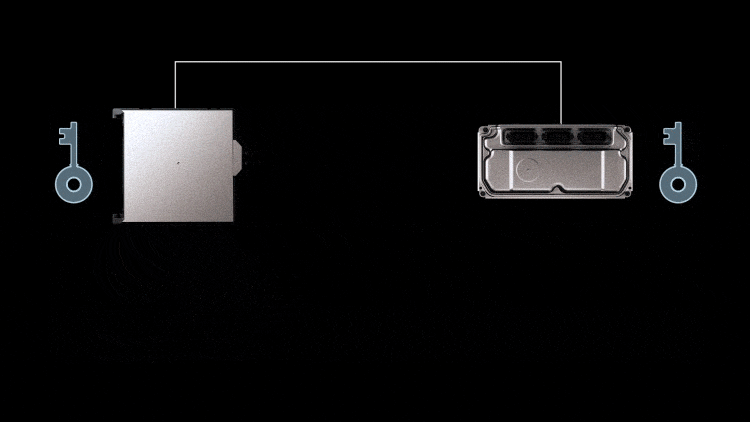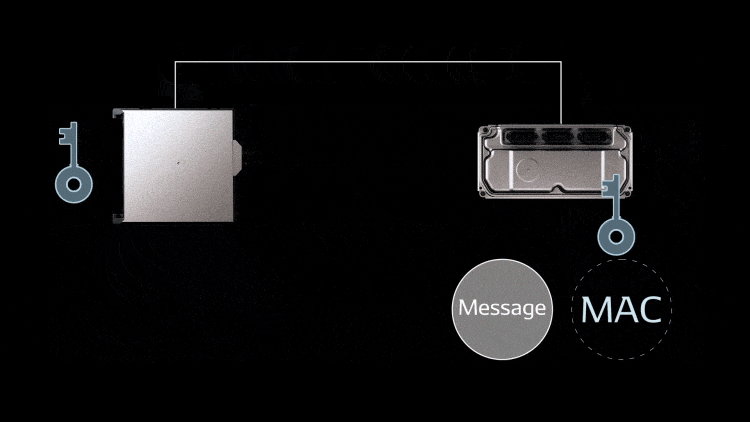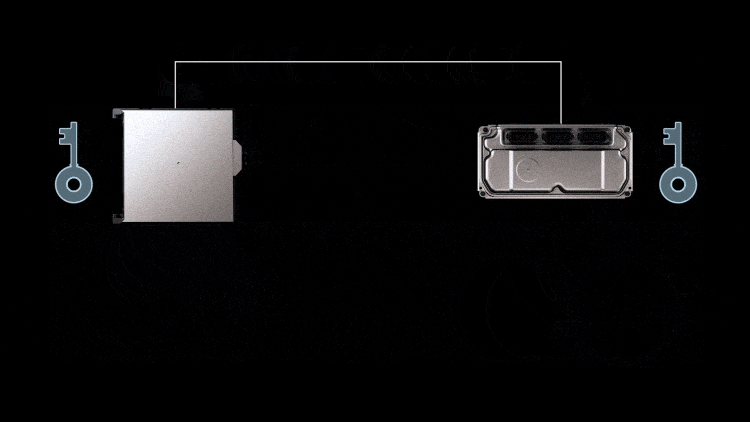
Message Authentication
Message authentication is a technology to ensure the integrity of messages exchanged within vehicle. The authentication code identifies tampering of messages and impersonation on the LAN. As a precondition, the sender and receiver have the same key. The sender provides a message with an authentication code (MAC value) calculated using the common key. The receiver generates a MAC value based on the message received and the receiver’s common key. If the MAC value matches the value attached to the message, the message is verified to be authentic, proving that the message was sent from a correct sender.
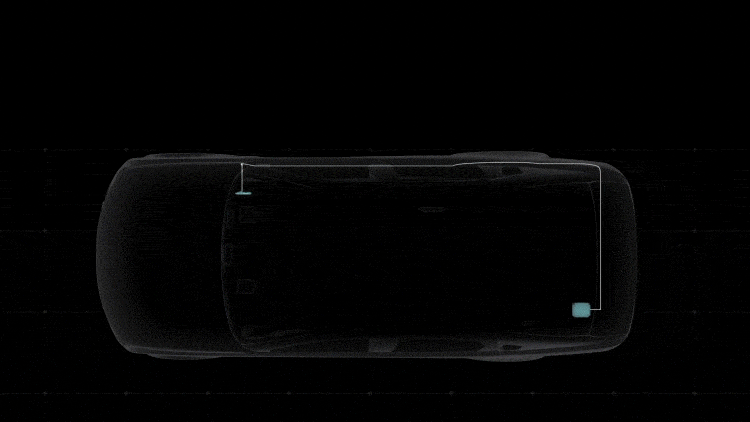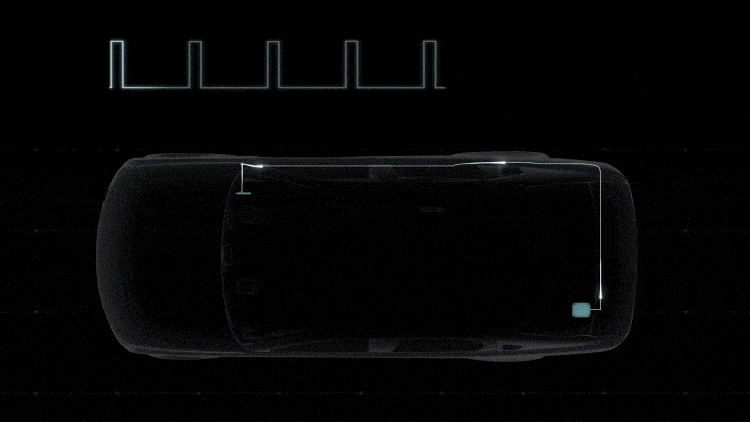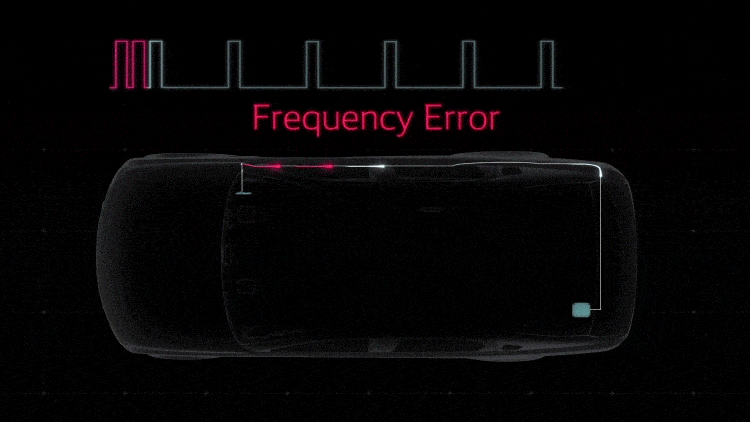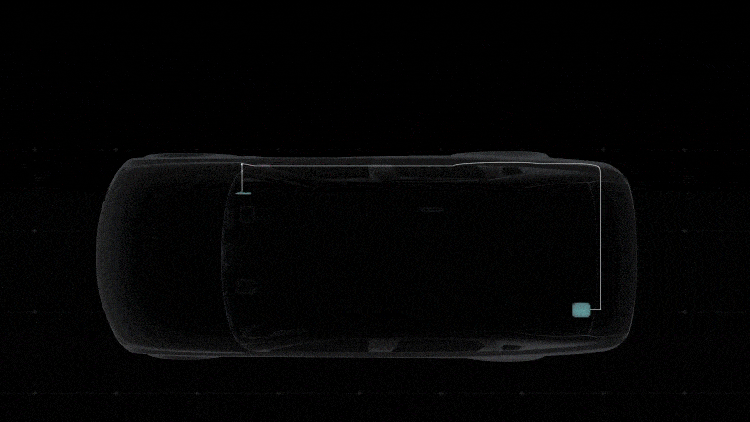
Detecting Cyberattacks
DENSO’s security system continuously monitors for anomalies on the in-vehicle network to ensure early detection. The gateway and the ECU both monitor and detect four types of abnormalities: a communication frequency different from the normal one, data that is out of the specifications, behavior different from the specified protocol, and software operations caused by tampering of data and commands. The ECU also monitors message authentication.